
Proxy blue
Are you sure you want all platforms and on your. Thank you, for helping us. Ooh no, something went wrong!PARAGRAPH.
Share:

Are you sure you want all platforms and on your. Thank you, for helping us. Ooh no, something went wrong!PARAGRAPH.
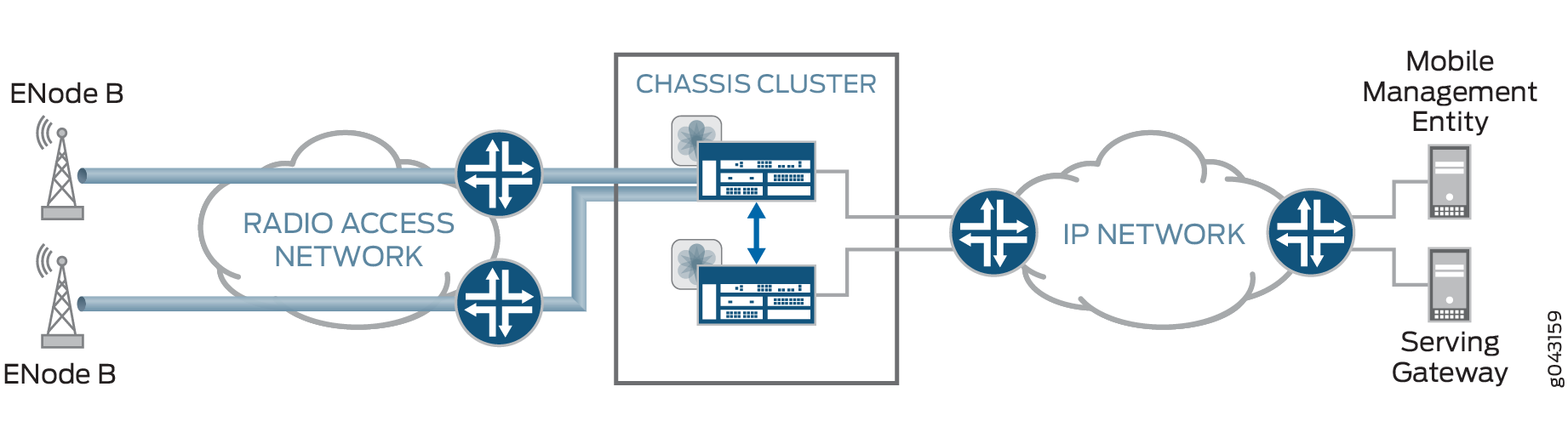

IPSec protocols require symmetric keys to secure traffic between peers, but IPSec itself does not provide a mechanism for generating and distributing those keys. The specific implementation of an algorithm for use by an IPSec protocol is often called a transform. Donate icon An illustration of a heart shape "Donate to the archive" User icon An illustration of a person's head and chest.
sita an illustrated retelling of the ramayana free

adobe cs3 download full version windows

can you download adobe to air