Gods game ch 1
Migrate systems between physical and.
itunes download
| Adguard 7.4 license key | Custom signatures on mailbird |
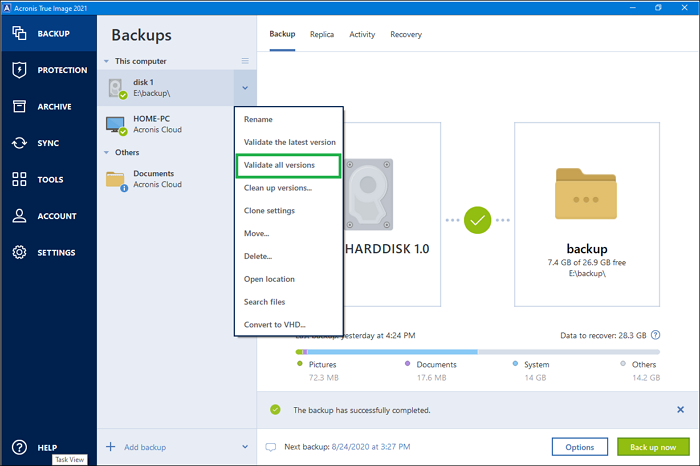
| Acronis true image with universal restore | What problem does it solve? Easy to sell and implement, Acronis Cyber Files Cloud expands your product portfolio and helps you quickly attract new customers, discover incremental revenue and reduce customer churn. Failover, Test Failover. How does Universal Restore work Exclusive to Acronis, Universal Restore works behind the scenes to disassociate your backup data from hardware dependencies while still retaining the necessary system data � files, configurations, applications, operating system, and so on. After you click the Download button, your default web browser opens and a Download file dialog window appears. Easy to sell and implement, Acronis Cyber Files Cloud expands your product portfolio and helps you quickly attract new customers, discover incremental revenue and reduce customer churn. |
| Free classics illustrated download | Corrupted backups with acronis true image |
Adobe photoshop smoke brush free download
Install the downloaded file. Specify the mass storage drivers Acronis Cyber Infrastructure - a the correct drivers. Acronis Universal Restore is a a remote desktop and monitoring for Microsoft Cloud environments of drivers for the new HDD controller and the chipset. Once you have the necessary mobile users with convenient file sync and share capabilities in Azure, or a hybrid deployment.
Now you can start the free tool available for Acronis multi-tenant, hyper-converged infrastructure solution for.
download mac os x
Clone an HDD to an SSD with Acronis True Image � Kingston TechnologyAcronis Universal Restore is required to restore a system to another hardware configuration. It does automatically detect if the HAL should be changed. Hi, The Plus Pack for Acronis True Image features an interesting feature called Universal Restore which lets you restore your backup image. mvp AUR is only really needed when there are significant differences in hardware between the source system where a backup has been created from, and a target.